Security First: What “SOC 2” and “HIPAA-Ready” Really Mean for Your Clinic
What those security labels really mean, how to verify claims, and how to choose the best vet software with confidence

Why this matters when you are choosing the best veterinary software
If your practice is shopping for the best vet software, your short list probably includes a cloud practice management system, client communication tools, payment processors, AI scribes, and phone systems. Every one of these touches sensitive information about clients, patients, or money. That makes your hospital an attractive target. The AVMA has warned that roughly 11,000 veterinary practices a year experience a cyberattack, which works out to more than 200 clinics every week. If you have not seen a headline locally, it is because many events go unreported. This is a financial and operational risk, not just a technical one. (American Veterinary Medical Association)
Security language on vendor websites can feel like alphabet soup. Two phrases you will see often are “HIPAA-ready” and “SOC 2.” This article translates those terms into plain language and gives you precise steps to verify claims during demos so you can choose the best veterinary software for your team and your clients.
The short version
-
HIPAA-ready is a marketing phrase. HIPAA is a U.S. law that protects human health information. Veterinary clinics are generally not covered entities under HIPAA. You should still demand strong privacy and security, but do not pay for “HIPAA compliance” that does not apply to you. (HHS.gov)
-
SOC 2 is an independent audit of a vendor’s controls for security, availability, processing integrity, confidentiality, and privacy. Treat a SOC 2 report like a lab result. Read the details, do not rely on the sticker. (aicpa-cima.com)
-
Card payments mean PCI, not HIPAA. If your clinic takes cards, your software and merchant provider must follow PCI DSS. That is a different standard. (PCI Security Standards Council)
First principles, what is HIPAA and who must comply
HIPAA protects the privacy and security of protected health information about people, such as a patient’s medical history, lab results, or insurance details. It applies to covered entities like health plans, healthcare clearinghouses, and healthcare providers who transmit certain electronic transactions. It also applies to their business associates. Veterinary clinics treat animals, which are not “individuals” under HIPAA, therefore typical veterinary records are not subject to HIPAA. (HHS.gov)
Some reputable veterinary bodies make this explicit. For example, AAHA’s telehealth guidance states that veterinary practices do not have to be HIPAA compliant, while confidentiality is still required under state practice acts and business rules. That means your clinic should protect client data, even if HIPAA itself does not apply. (AAHA)
There are rare edge cases. If information about an animal could identify a human subject inside a human provider’s HIPAA record set, HIPAA protections can attach to that specific context, for example service animals documented within a human hospital’s patient record. That is not the same as HIPAA applying to your veterinary medical records. (The HIPAA Journal)
Bottom line for buyers evaluating the best vet software.
-
Expect privacy and security that meets or exceeds human healthcare norms, but recognize that “HIPAA-ready” is not a legal requirement for your clinic.
-
Focus your evaluation on the vendor’s actual controls, their data handling practices, and their willingness to sign the right agreements for your use case, for example a BAA if they truly operate as a business associate to a human covered entity you work with. (HHS.gov)
What “HIPAA-ready” usually means in a sales deck
Because many customers in human healthcare ask for HIPAA, SaaS vendors often build controls that align with HIPAA’s Security Rule, for example encryption, access controls, audit logging, and breach procedures. When you see “HIPAA-ready,” translate that as “we have controls similar to what HIPAA expects.” This can be a good sign, but it is not proof of compliance, and it may not be relevant to your legal obligations as a veterinary clinic. Ask for specifics.
Questions for vendors
-
Which HIPAA Security Rule controls do you implement, and how are they monitored, for example MFA, unique user IDs, audit logging, and automatic log review
-
Will you sign a Business Associate Agreement if we need one for a specific human healthcare integration, and under what scope, for example limited to a given feature or integration
-
How do you handle client contact data, for example names, emails, phone numbers, addresses, which is personally identifiable information even if not PHI
If the vendor cannot answer clearly, treat “HIPAA-ready” as a sticker, not a safeguard.
SOC 2 in plain English
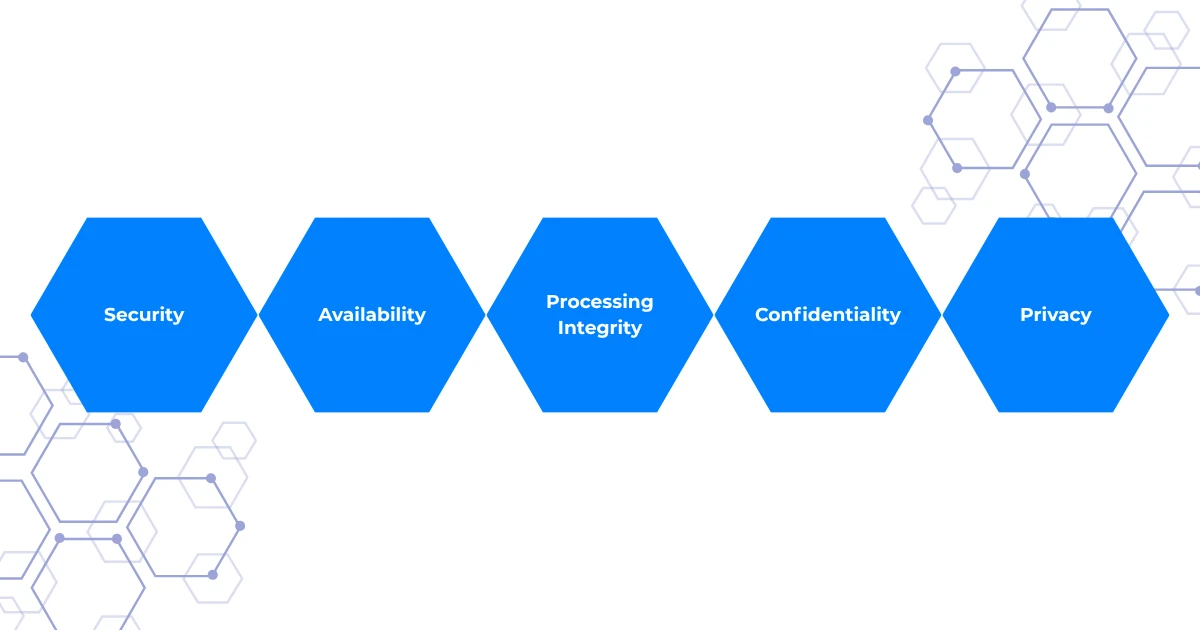
SOC 2 is a report issued by an independent auditor, typically a CPA firm, that evaluates a service organization’s controls relevant to five Trust Services Criteria, which you will see abbreviated as Security, Availability, Processing Integrity, Confidentiality, Privacy. Vendors commonly scope to Security only, sometimes to three or all five. (aicpa-cima.com)
There are two flavors.
-
Type I evaluates whether controls are designed properly at a point in time.
-
Type II evaluates whether those controls were designed and also operated effectively over a defined period, for example 6 to 12 months. For buyers, Type II is more valuable because it shows sustained operation, not just design. (Secureframe)
A solid SOC 2 gives you evidence that a vendor has processes for identity and access management, change management, vulnerability management, incident response, backup and recovery, and more, aligned to the chosen criteria. It does not guarantee zero breaches, just like a clean lab test does not guarantee perfect health.
How to read a SOC 2 like a pro, five minutes to the truth
Ask for the full SOC 2 report under NDA, not just a marketing summary. Then scan these sections.
-
Scope. Which products, environments, and locations are included. Are you buying the thing that was audited
-
Type and period. Type I or Type II. If Type II, confirm the period covers the last 6 to 12 months, not years ago
-
Trust Services Criteria. Only Security, or also Availability, Confidentiality, etc
-
Subservice organizations. Cloud providers like AWS, authentication providers like Auth0, payment processors. Are they included or carved out
-
Complementary user entity controls, CUECs. The report will list controls you must run in your clinic for the vendor’s controls to be effective, for example configuring password policies or role-based access correctly
-
Exceptions and findings. Read the deviations. Are they minor, for example a missing training acknowledgment, or material, for example unpatched critical vulnerabilities
-
Bridge letter. If the report period ended months ago, ask for a bridge letter that asserts there were no material changes post-period
These basics will help you differentiate strong vendors when you compare the best veterinary software options. (aicpa-cima.com)
How SOC 2 maps to real clinic risks
-
Ransomware and data loss. Availability and Security criteria require tested backups, restricted access, and incident response. AVMA’s guidance shows how common cyberattacks are for clinics. Treat backup testing and offsite recovery like oxygen. No backup plan, no deal. (American Veterinary Medical Association)
-
Unauthorized access. Security criteria cover MFA, least privilege, and logging. Ask vendors to show audit trails for user access and changes.
-
Data leakage. Confidentiality and Privacy criteria address encryption, data retention, and secure disposal. Confirm at-rest and in-transit encryption and ask for data retention defaults that fit veterinary recordkeeping norms.
You can also look at broader healthcare attack patterns. In 2023, healthcare organizations were the most targeted sector for ransomware among critical infrastructure categories, according to FBI data reported by Axios. That pressure pushes attackers downstream to smaller clinics and specialty providers, which includes veterinary. (Axios)
Payments change the rules, PCI DSS, not HIPAA
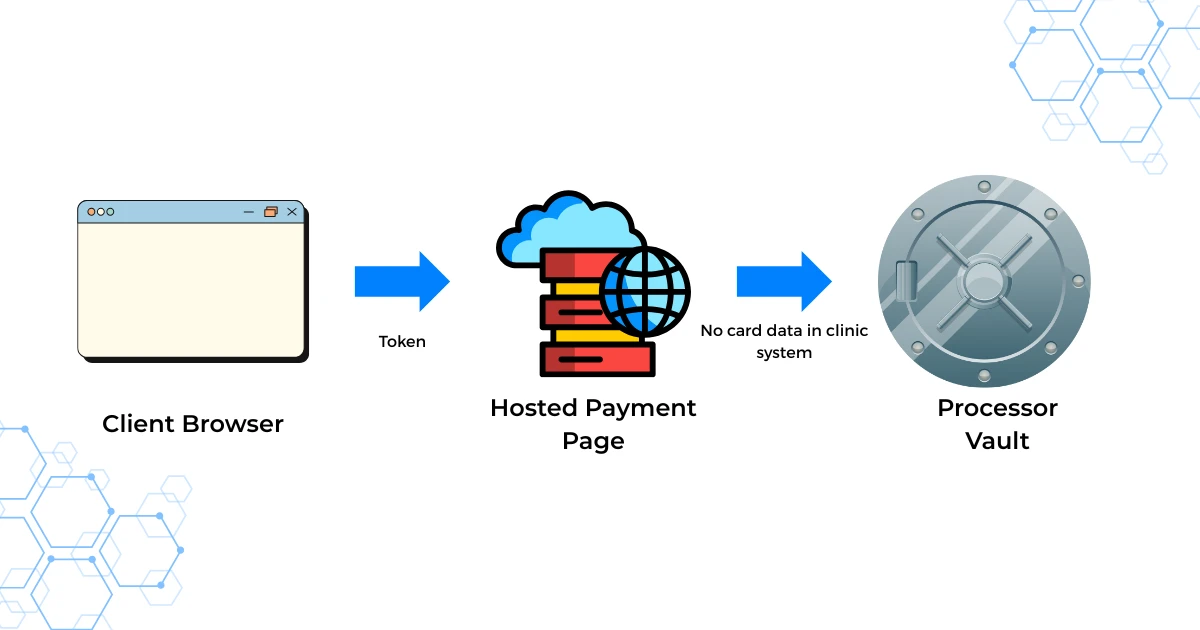
If you accept credit and debit cards, you must handle data in a way that aligns with the Payment Card Industry Data Security Standard, PCI DSS. Your payment vendor and merchant acquirer will guide your specific validation steps, which may include a Self-Assessment Questionnaire. This has nothing to do with HIPAA. It is a card brand and acquirer requirement. Make sure your software vendor’s approach keeps card data out of your environment whenever possible, for example tokenization and hosted fields. (PCI Security Standards Council)
State confidentiality rules still matter
Although HIPAA does not cover veterinary records, many states have confidentiality rules for the veterinarian-client-patient relationship. You also have general obligations around personal information, for example names, emails, and phone numbers. In other words, your clinic still needs strong privacy and security, even without HIPAA. (AVMA Journals)
Red flags to watch for on any “best vet software” shortlist
-
Vague claims like “bank-level security” without specifics
-
“HIPAA-ready” with no control detail, no policies available under NDA
-
SOC 2 “in progress” for more than 12 months, or only Type I after years in market
-
No MFA option for staff logins or portal access
-
No documented backup and recovery testing
-
No published uptime target or incident history
-
Shared logins encouraged for staff to “save seats”
-
No audit trails for who accessed what and when
-
No breach notification process and no responsible disclosure policy
Green flags that separate leaders from the pack
-
SOC 2 Type II covering Security plus at least one of Availability or Confidentiality, within the last 12 months
-
Clear scope in SOC 2 that includes the product you are buying
-
MFA enforced by default, SSO support for larger groups
-
Role-based access control with least privilege presets
-
Immutable audit trails and offsite, encrypted backups with restore drills
-
Field-level encryption for high-sensitivity fields where applicable
-
Clear data retention controls, for example automated purge after X years
-
Documented incident response and a status page with history
-
PCI-aware payment flows that keep card data out of your network, for example tokenization, hosted pay pages, and vaulting with the processor (PCI Security Standards Council)
Vendor questionnaire you can paste into your next demo
Use these as yes or no plus “show me.” Ask them to screen-share and prove it.
-
Do you have a current SOC 2 report, Type II preferred, covering the specific product we are buying
-
Which Trust Services Criteria are in scope, Security is required, do you also include Availability or Confidentiality
-
What is the report period end date, can you provide a bridge letter
-
Do you enforce MFA by default for all clinic users, and can we require it
-
Do you support SSO, for example Microsoft Entra ID or Google Workspace
-
How do you manage least privilege, can we assign roles that restrict access to billing or medical notes
-
What audit logs exist for user logins, data access, changes, and exports
-
How long are logs retained, can we export them on request
-
Describe your backup strategy, frequency, encryption, and restore test cadence
-
Are databases encrypted at rest, and is all network traffic encrypted in transit, for example TLS 1.2 plus
-
Do you isolate each tenant’s data logically or physically
-
How do you handle data retention, purging, and client requests for deletion where appropriate
-
What is your incident response plan and customer notification window
-
Do you maintain a public status page with uptime history
-
If you process card payments, how do you keep card data out of our environment, and which PCI scope applies to our clinic, SAQ A, SAQ B, SAQ P2PE, etc (PCI Security Standards Council)
Translating marketing to reality across common veterinary software categories
Cloud practice management systems, PIMS
-
Expect SOC 2 Type II with Security and Availability
-
Confirm daily encrypted backups, restore tests, and geographic redundancy
-
Verify audit logging for medical record access and edits
-
Ask about integrations, for example lab, imaging, AI scribes. Third parties can add risk, check how they are vetted in the vendor’s SOC 2 subservice listing (aicpa-cima.com)
Client communication and marketing suites
-
These tools house bulk client contact info and messaging history
-
Confirm opt-in, opt-out, and retention controls
-
Validate export controls, for example to share data with your CRM safely
-
“HIPAA-ready” claims are less relevant to a veterinary clinic, focus on security controls and data handling, not the label (AAHA)
Payment links, terminals, and online checkout
-
Ask where card data flows and which party is PCI validated
-
Prefer solutions that outsource card data capture to the processor’s hosted pages or embedded fields
-
Your acquirer can confirm your exact validation path. Do not assume your vendor’s claim covers you automatically (PCI Security Standards Council)
Phone systems and call recording
-
Call recordings can include personal information
-
Confirm encryption, access controls, retention limits, and easy redaction
-
For AI call summaries, ask where audio is stored, for how long, and how models are secured
AI scribes and dictation
-
Ask whether models are vendor-hosted or third party
-
Confirm data segregation, training data policy, and deletion timelines
-
Ask whether the AI vendor appears as a subservice organization in the PIMS or scribe provider’s SOC 2 report, and whether that risk is included or carved out (aicpa-cima.com)
A note on ISO 27001 and other frameworks
You may see ISO 27001, a global standard for information security management systems, instead of SOC 2. This is also meaningful. ISO requires a certified ISMS and periodic audits. Many strong vendors hold either SOC 2 or ISO 27001, sometimes both. Do not force both. Focus on whether the cert or report covers the product you are buying and whether the controls match your risk.
Your clinic’s responsibilities, do not skip these
SOC 2 reports include complementary user entity controls, which spell out what the customer must do. If you skip these, the vendor’s controls cannot fully protect you.
-
Enforce unique accounts, MFA, and strong passwords
-
Use role-based access and remove access immediately when staff leave
-
Review audit logs and exports, especially for high-risk roles
-
Maintain secure endpoints, for example patched Windows or macOS, full-disk encryption, and EDR
-
Train staff on phishing and social engineering
-
Test your own backup of critical data exports, for example monthly CSV of client contact info stored in a secure vault as an emergency fallback
Bringing it back to your buying decision, how to rank the best veterinary software
When two vendors look similar on features and price, security diligence often reveals a clear leader. Weight security as part of your scoring model instead of treating it like a checkbox.
Simple scoring suggestion
-
SOC 2 scope and recency, 0 to 3 points
-
MFA, SSO, RBAC defaults, 0 to 3 points
-
Backup, restore proof, and incident history, 0 to 3 points
-
Logging, export controls, retention, 0 to 3 points
-
PCI alignment for payments, 0 to 3 points
Add security to your overall “best veterinary software” rubric so marketing momentum does not outrun risk awareness. (PCI Security Standards Council)
Copy-paste email template to request evidence
Subject, Security documentation request for VetSoftwareHub evaluation
Hello,
We are evaluating [Product] as part of our search for the best veterinary software for our clinic. To complete security due diligence, please provide the following under NDA.
-
Most recent SOC 2 report, Type II preferred, including scope and subservice organizations
-
Security whitepaper or summary of controls for authentication, logging, backups, and incident response
-
Data retention defaults and options for our tenant
-
If applicable, your PCI DSS approach for hosted payments and our expected SAQ type
-
Contact for security incidents and a link to your status history page
Thank you,
[Name], [Practice], [Contact]
Common myths, quick corrections
-
Myth: Veterinary practices must be HIPAA compliant
Correction: HIPAA covers human PHI held by covered entities and their business associates. Veterinary clinics are not covered entities, though state confidentiality rules and general privacy laws still apply. (HHS.gov) -
Myth: A SOC 2 badge guarantees security
Correction: SOC 2 is an audit report, not a guarantee. Read the scope, type, period, exceptions, and CUECs. (aicpa-cima.com) -
Myth: Using a third party payment link removes all PCI responsibility
Correction: Outsourcing reduces scope but does not remove your obligations. Your acquirer and the card brands define your validation path. (PCI Security Standards Council)
Action checklist for your next purchase
-
Add a “Security” section to your RFP or demo script
-
Ask for the SOC 2 report, read scope and exceptions
-
Require MFA and role-based access for every user
-
Confirm backups and restore drills, ask for dates
-
For payments, confirm PCI approach and keep card data out of your network
-
Document your own CUECs, for example offboarding checklist, log review cadence
-
Decide using a balanced score that includes security and uptime, not just price and features
Do this for PIMS, client comms, phones, imaging, AI scribes, and any integration that touches your data. Security first is how you choose the best veterinary software for your hospital with confidence.
Final take
Security is not a sticker, it is a system. “HIPAA-ready” can be a signal, but it is not your rulebook. SOC 2 can be excellent evidence, but only if you read the scope, type, period, and exceptions. Payments bring PCI into the picture, not HIPAA. Add these checks to your demo script and scoring so you can pick the best veterinary software with confidence and protect your clinic from the risks that hurt most, downtime, data loss, and lost client trust. (aicpa-cima.com)
Citations
-
HHS, Covered entities and business associates. (HHS.gov)
-
HHS, Summary of the HIPAA Privacy Rule. (HHS.gov)
-
AAHA telehealth guidance on security and confidentiality for veterinary practices. (AAHA)
-
AICPA, SOC 2 overview and Trust Services Criteria. (aicpa-cima.com)
-
PCI Security Standards Council, merchant guidance and small merchant guide. (PCI Security Standards Council)
-
AVMA, cyberattack prevalence in veterinary practices. (American Veterinary Medical Association)
-
Axios summary of FBI IC3 ransomware report for healthcare context. (Axios)

Adam Wysocki
Contributor
Adam Wysocki, founder of VetSoftwareHub, has 30 years in software and almost 10 years focused on veterinary SaaS. He creates practical frameworks that help practices evaluate vendors and avoid costly mistakes.
Connect with Adam on LinkedIn